Mastering KYC Standards: An Exhaustive Manual on Procedures, Legal Frameworks, and Tech Integration

Mastering KYC Standards: An Exhaustive Manual on Procedures, Legal Frameworks, and Tech Integration
KYC Compliance: A Comprehensive Guide
August 19, 2024
Over the last few decades, financial crime has ballooned into its own multi-trillion-dollar industry. The National Council on Identity Theft Protection estimates that 33 percent of Americans have fallen victim to a form of identity theft in their lives. And, according to Europol, between two and five percent of global GDP is laundered each year. As a result, Know Your Customer—also referred to as Know Your Client or simply KYC —procedures have become a critical function to prevent criminal financial activities and comply with international Anti-Money Laundering (AML) laws.
KYC refers to the steps a business, typically a financial institution, takes to establish a customer’s identity, investment understanding, and risk profile. For example, KYC checks are mandatory when a customer opens a new account, and obligated entities follow stringent protocol to adhere to international KYC/AML regulations.

In this article, we’ll explain what KYC is, the KYC process, why it’s important, and how you can leverage technology to manage the risk of financial crime and ensure regulatory compliance.
Jump to:
What is KYC compliance?
KYC compliance laws
KYC requirements by industry
Steps to implementing a compliant KYC process
KYC challenges
KYC compliance in the digital age
Frequently asked questions
What is KYC compliance?
KYC is a set of guidelines and regulations that financial institutions use to verify customers. The procedures involve establishing each customer’s identity, suitability, financial profile, and the potential risks of engaging with them. The objective is to identify illegal activity such as fraud, money laundering, and financial terrorism before it occurs. Although KYC is considered an ethical practice that helps to build trust with customers, these checks are also a critical legal requirement for banks and financial service companies to ensure regulatory compliance.
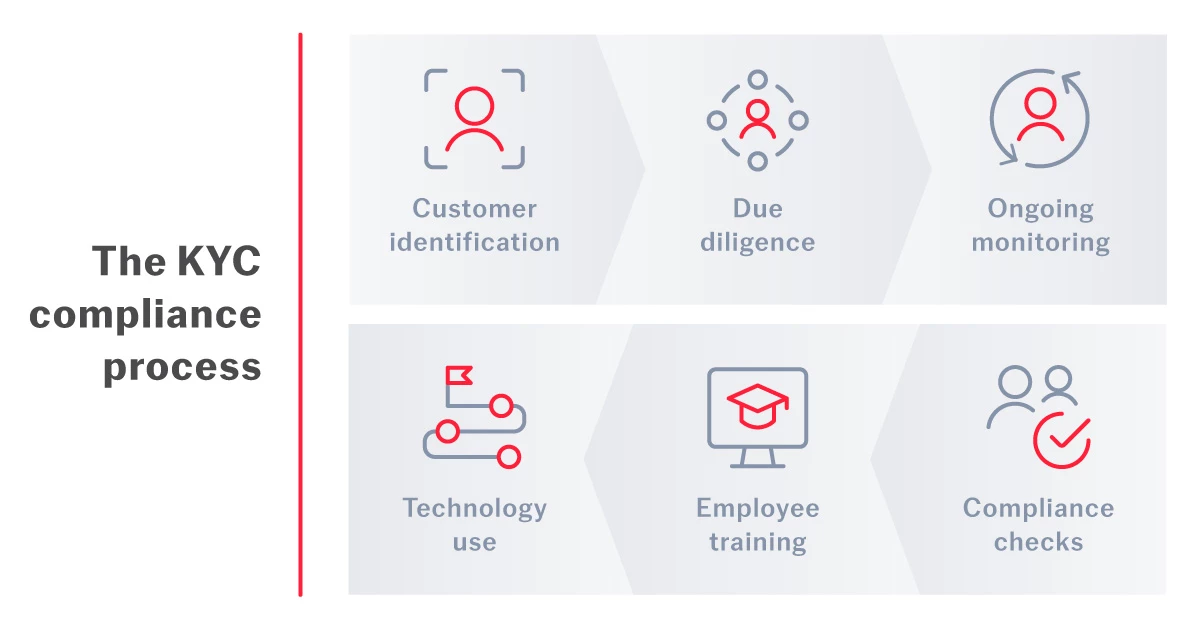
There are three key components of KYC:
- Customer Identification Program (CIP): CIP requires financial institutions to collect and verify the basic identity information of a customer, including their name, address, and date of birth. This process helps the institution accurately verify customers and assess the risks linked to their accounts.
- Customer Due Diligence (CDD): CDD is the next stage of KYC. It involves understanding the customer’s financial behavior and transaction patterns to create a risk profile. High-risk customers must undergo Enhanced Due Diligence (EDD), with more thorough background checks and continuous monitoring.
- On-going monitoring: Continuous monitoring involves overseeing financial transactions and accounts based on the customer’s risk profile. Institutions may look at activities such as spikes in transaction activity or unexpected cross-border activities.
KYC compliance laws
The rules around KYC are governed by several national and international laws. Most KYC laws fall under AML regimes. These regimes are based on the recommendations of the Financial Action Task Force (FATF), a pan-government organization formed to fight money laundering, terrorism, and proliferation financing.
In the United States, there are four key laws and regulatory bodies overseeing KYC compliance:
- The Bank Secrecy Act (BSA) of 1970: Under BSA, financial institutions are required to record cash purchases, report cash transactions over $10,000, and flag suspicious activity.
- The USA PATRIOT Act of 2001: This Act broadened BSA requirements. It incorporated CIP into KYC procedures, strengthening customer due diligence and verification to combat terrorism financing and money laundering.
- Financial Crimes Enforcement Network (FinCEN): FinCEN, and the Office of Foreign Assets Control (OFAC), sets standards and shares guidance for KYC compliance.
- Financial Industry Regulatory Authority (FINRA): Under the PATRIOT Act, broker-dealers must have an AML compliance program. FINRA provides AML program guidelines, including those that involve a risk-based approach to customer verification.
Some of the other key international KYC laws include:
- The European Union’s Anti-Money Laundering Directives (AMLD), which outlines comprehensive KYC and AML requirements for EU member states.
- The Money Laundering Act – 2017 (MLA) governs the UK, defining customer verification rules for reporting entities.
- Proceeds of Crime (Money Laundering) and Terrorist Financing Act (PCMLTFA) of Canada sets the KYC requirements and rules for reporting entities.
KYC requirements by industry
KYC compliance laws apply to global businesses across a range of industries, with some industries implementing more stringent rules in recent years. Some of the biggest industries required to comply with KYC are:
Banking
KYC was created for banks and financial institutions, so companies in the banking sector face the strictest compliance requirements. Bankers and advisors are required to identify
- their customers;
- beneficial owners of businesses; and
- the purpose and nature of customer relationships.
Banks also have to check customer accounts for suspicious or illegal activity and continuously ensure the accuracy of the accounts.
Financial services
Much like the banking sector, there are strict KYC rules for financial services organizations. They’re required to verify the identity of their customers, understand the nature of their financial activities, and ascertain risk profiles through KYC checks. To comply with AML regulations and prevent financial crimes, they also need to continuously monitor customers’ transactions, maintain detailed records, and report suspicious activities.
Cryptocurrency
Cryptocurrency companies are classified as money services businesses (MSBs), so they also have to comply with some AML laws. This involves:
- Implementing customer identification programs
- Maintaining specific reporting and record-keeping procedures
Since fiat-to-cryptocurrency exchanges facilitate transactions involving both national currencies and cryptocurrencies, they’re required to follow KYC measures to ensure compliance. In December 2020, FinCEN proposed regulations mandating cryptocurrency market participants to verify, maintain, and submit records of customer identities. This rule categorizes specific cryptocurrencies as monetary instruments, subjecting them to KYC requirements. The proposition is scheduled for approval in 2024.
Insurance
To comply with KYC regulations, insurance companies must verify the identity of policyholders and beneficiaries, and conduct due diligence to prevent money laundering and terrorist financing. The USA PATRIOT Act also mandates insurers to establish AML programs, report suspicious activities, and maintain comprehensive records.
Real estate
Under KYC regulations, real estate professionals should perform customer due diligence to prevent money laundering. Real estate businesses in the US must also comply with AML regulations when conducting transactions through financial institutions. FinCEN is authorized to issue Geographic Targeting Orders (GTOs) in high-risk jurisdictions, mandating insurance companies to identify the individuals behind companies or entities used in high-value or cash real estate transactions.
Steps to implementing a compliant KYC process
The KYC process begins with the Customer Identification Program (CIP), where financial institutions gather a customer’s basic identifying information:
- Name
- Date of birth
- Address
- Identification number
Institutions will typically gather this information when the customer opens an account, but they’re required to verify the account holder’s identity “within a reasonable time.” Customer identification is carried out by verifying documents like passports, driver’s licenses, or social security numbers, and sometimes using non-documentary methods like database checks.
Customer Due Diligence (CDD) is the next stage, where institutions will ascertain more information about the customer’s financial behavior and transaction patterns to develop a risk profile for them. If a customer is high risk, at this stage, the institution will perform Enhanced Due Diligence (EDD), involving in-depth background checks and monitoring. Organizations keep comprehensive records of all this KYC information.
A critical, lesser discussed component of the KYC process is ongoing monitoring, where customer transactions are continuously observed to spot unusual activities. Any suspicious transactions or behavior is then reported to the relevant authorities. Institutions will also carry out periodic reviews to ensure customer information is up-to-date and accurate.
Institutions will train employees and use technology to streamline and improve their KYC procedures, ensuring compliance with regulations and minimizing the risk of financial crimes.
Develop a KYC policy
Developing a robust KYC policy is essential to ensure compliance with international regulations against fraud, money laundering, and terrorist financing. Having clear measures for implementing KYC also helps to foster more secure financial transactions.
Financial institutions usually base their KYC policies on four key elements:
- Customer policies
- Customer identification procedures, including identity checks, verification, data collection, Politically Exposed Persons (PEPs) and sanctions lists checks
- Risk assessments and management
- Ongoing monitoring and record-keeping
Conduct employee training
Employee training is critical for communicating, controlling, and safeguarding knowledge of Anti-Money Laundering / Countering the Financing of Terrorism (AML/CFT) and KYC requirements within an organization. At a minimum, training in these areas should cover:
- Ways that money laundering and terrorist financing may be carried out with the company’s products and services
- Internal policies to prevent fraud, money laundering, and terrorist financing, and to escalate suspicious activity
- General information on AML/CFT and KYC regulatory compliance requirements
- How to identify and report transactions to a regulator or authority
Implement a robust Customer Identification Program (CIP)
A successful Customer Identification Program (CIP) hinges on thorough risk assessments at both the institutional and individual account level. Global CIP guidelines offer useful directions which should lay the foundation for every CIP policy. However, it’s the responsibility and discretion of each institution to define its own risk levels and internal policies. Like other AML compliance measures, CIPs should be clearly and formally documented to guide all employees and satisfy regulatory requirements.
To create a CIP that’s robust and tailored to your institution’s risk-based approach, you’ll need to consider factors such as:
- The types of account you offer
- Account opening methods
- Available identification information
- The size of your institution
- Your institution’s location and customer diversity across different geographic areas
Leverage advanced KYC technology
Financial services institutions face a unique set of challenges. Crimes, such as fraud, terrorist activity, and money laundering, are committed by bypassing banking processes or using suspicious documents, resulting in billions of dollars in fines and legal risks. Although evolving regulations aim to solve these problems, these institutions often find themselves with fractured processes and repetitive due diligence requests, causing further problems, including:
- Longer onboarding times
- Higher service costs
- Decreased customer satisfaction
- Increased risk of non-compliance with KYC
ABBYY Timeline , our advanced AI-powered process intelligence platform, is a comprehensive solution designed to target these vulnerable areas in KYC processes:
- Increased process transparency. Timeline helps financial institutions discover complex interactions between customers, employees, processes, and content. It gathers the necessary data on end-to-end processes to help you identify opportunities for improvement, and ensure ongoing compliance monitoring.
- Streamlined onboarding. KYC begins with initial contact, from customer account creation to document authentication. Integrating onboarding with customer interactions can detect suspicious activity. ABBYY intelligent document processing (IDP) automates document intake for KYC compliance.
- Full process visibility. ABBYY Timeline goes beyond just visualizing processes—it uncovers crucial human and content interactions. It shows where customers and employees engage, input, review, and decide on critical content, enabling you to identify content types and interaction patterns to flag suspicious activity.
- Rapid crime and fraud detection. Banks are most vulnerable to potential crimes and fraud due to process loopholes and suspicious documents. ABBYY process mining and IDP help banks identify and counter these vulnerabilities early, establishing document authenticity from the start.
Request a demo to find out how ABBYY Timeline could improve your KYC compliance process and streamline your business critical processes.
KYC challenges
While KYC regulations are designed to be clear and robust, there are increasing challenges to implementing them.
A benefit of the international commitment to preventing financial crime is that legislation is regularly updated to mitigate industry risks. However, evolving regulations put pressure on organizations to continually update their policies and processes. Aside from the red tape involved in adapting internal governance processes, adhering to regulatory developments is often costly as it involves retraining staff, updating documentation, and, at times, upgrading systems.
In addition, with the increasing significance of data privacy, regulators are imposing stricter rules on businesses to safeguard customer data and use KYC information solely for its intended purpose. Balancing due diligence to protect customer data, while fielding the risks of financial crime, can be difficult to balance. Coupling these challenges with the growing digitization of the KYC process, it can be difficult for institutions to keep up with regulations.
KYC compliance in the digital age
Digital transformation across KYC compliance processes has led to the advent of eKYC, where businesses use online processes to verify customer identities and transactions. Financial services companies increasingly use mobile and web-enabled solutions that incorporate on-device technology and biometric authentication (such as facial recognition) to accurately identify customers in the digital environment.
The combination of cutting-edge technology, compliant machine learning, and identity expertise has established eKYC as a legally recognized form of identification, extensively employed for AML compliance. For instance, in India, the use of eKYC is facilitated by Aadhaar, the national biometric eID scheme. It covers 99.9% of the adult population, providing swift and reliable customer onboarding and verification.
At the forefront of digitizing KYC processes, ABBYY’s AI-driven solutions are built to support digital KYC compliance for financial services companies that want to implement seamless and secure online and mobile identity proofing .
Your customers will be able to onboard through their mobile or desktop, helping you to reduce abandonment rates and customer churn. Paired with our intelligent document processing solutions, you can automate your most data-heavy processes and implement continuous monitoring.
Frequently asked questions
What documents are typically required for KYC verification?
A critical step in the KYC process is customer identification. The documents that are typically required include:
- A government-issued photo ID, such as a passport, driver’s license, or national ID card
- Proof of address, such as a utility bill or bank statement
- Social security number or tax Identification number (in some instances)
These documents help to verify a customer’s identity, address, and financial legitimacy.
What are the benefits of automating the KYC process?
Streamlining and automating your KYC processes is an invaluable way to minimize the risk of errors and improve business efficiency.
With technologies like intelligent document processing and process mining , you can automate the document intake processes for customer onboarding, according to KYC/AML legislation and best practices. This will help you ensure consistent compliance with regulations, improve fraud detection through real-time monitoring, and provide a seamless customer experience. You’ll also reap the benefits of lower operational costs, allowing you to allocate resources more effectively.
What is the difference between Customer Identification Program (CIP) and Customer Due Diligence (CDD)?
CIP is typically the first stage of a KYC process. It involves a business collecting and verifying the basic identity information of a customer, including their name, address, and date of birth.
CDD is the next stage, where the business will do a deeper assessment of the customer to understand their financial behavior and transaction patterns. The institution will use this information to build the customer’s risk profile and begin ongoing monitoring.
What is Enhanced Due Diligence (EDD)?
EDD is an advanced due diligence check used to gather additional information on high-risk customers as part of the KYC process. It’s considered a more detailed next step after Customer Due Diligence (CDD). The aim of EDD is to gain a deeper understanding of a customer’s background and financial activity to prevent potential financial crimes. At times, EDD checks are related to a country’s unique legislation, and it’s up to individual businesses to determine their risk approach.
How often should customer information be updated?
One of the most important components of KYC is ongoing monitoring. Customer information should be updated periodically, based on the customer’s risk profile.
For low-risk customers, a business may want to update their records every few years, or whenever there are significant changes to the customer’s financial activity or information. For higher-risk accounts, customer information should be updated more frequently, for instance annually. Keeping the KYC data updated ensures compliance with regulations.
How can technology help with KYC compliance?
Technology enhances KYC compliance by enabling businesses to automate and digitize their most critical processes. Leveraging technologies such as AI , machine learning, and robotic process automation, you can automate key processes like onboarding. Automating tasks such as document intake, visualizing customer interactions, and performing customer identification checks digitally enables businesses to reduce the risk of errors and improve operational efficiency.
There are also numerous cost-related benefits of utilizing technology in KYC compliance. Technology reduces manual data entry, allowing employee resources to be reallocated. It also significantly accelerates the response time of your compliance controls and systems to promptly address factors like acquisitions, cost pressures, evolving regulations, and changes in internal or external structures.
How does ongoing monitoring work in KYC compliance?
In KYC compliance, ongoing monitoring involves continuously reviewing customer transactions and behavior. These reviews are usually based on the thresholds you set as part of the customer’s risk profile during onboarding. Having an awareness or expectation of each customer’s behavior helps institutions to detect unusual account activity and behavior. Any suspicious activities should be reported to relevant authorities to prevent financial crimes and adhere to regulatory compliance.
Subscribe for blog updates
First name*
E-mail*
Сountry*
СountryAfghanistanAland IslandsAlbaniaAlgeriaAmerican SamoaAndorraAngolaAnguillaAntarcticaAntigua and BarbudaArgentinaArmeniaArubaAustraliaAustriaAzerbaijanBahamasBahrainBangladeshBarbadosBelgiumBelizeBeninBermudaBhutanBoliviaBonaire, Sint Eustatius and SabaBosnia and HerzegovinaBotswanaBouvet IslandBrazilBritish Indian Ocean TerritoryBritish Virgin IslandsBrunei DarussalamBulgariaBurkina FasoBurundiCambodiaCameroonCanadaCape VerdeCayman IslandsCentral African RepublicChadChileChinaChristmas IslandCocos (Keeling) IslandsColombiaComorosCongo (Brazzaville)Congo, (Kinshasa)Cook IslandsCosta RicaCroatiaCuraçaoCyprusCzech RepublicCôte d’IvoireDenmarkDjiboutiDominicaDominican RepublicEcuadorEgyptEl SalvadorEquatorial GuineaEritreaEstoniaEthiopiaFalkland Islands (Malvinas)Faroe IslandsFijiFinlandFranceFrench GuianaFrench PolynesiaFrench Southern TerritoriesGabonGambiaGeorgiaGermanyGhanaGibraltarGreeceGreenlandGrenadaGuadeloupeGuamGuatemalaGuernseyGuineaGuinea-BissauGuyanaHaitiHeard and Mcdonald IslandsHoly See (Vatican City State)HondurasHong Kong, SAR ChinaHungaryIcelandIndiaIndonesiaIraqIrelandIsle of ManIsraelITJamaicaJapanJerseyJordanKazakhstanKenyaKiribatiKorea (South)KuwaitKyrgyzstanLao PDRLatviaLebanonLesothoLiberiaLibyaLiechtensteinLithuaniaLuxembourgMacao, SAR ChinaMacedonia, Republic ofMadagascarMalawiMalaysiaMaldivesMaliMaltaMarshall IslandsMartiniqueMauritaniaMauritiusMayotteMexicoMicronesia, Federated States ofMoldovaMonacoMongoliaMontenegroMontserratMoroccoMozambiqueMyanmarNamibiaNauruNepalNetherlandsNetherlands AntillesNew CaledoniaNew ZealandNicaraguaNigerNigeriaNiueNorfolk IslandNorthern Mariana IslandsNorwayOmanPakistanPalauPalestinian TerritoryPanamaPapua New GuineaParaguayPeruPhilippinesPitcairnPolandPortugalPuerto RicoQatarRomaniaRwandaRéunionSaint HelenaSaint Kitts and NevisSaint LuciaSaint Pierre and MiquelonSaint Vincent and GrenadinesSaint-BarthélemySaint-Martin (French part)SamoaSan MarinoSao Tome and PrincipeSaudi ArabiaSenegalSerbiaSeychellesSierra LeoneSingaporeSint Maarten (Dutch part)SlovakiaSloveniaSolomon IslandsSouth AfricaSouth Georgia and the South Sandwich IslandsSouth SudanSpainSri LankaSurinameSvalbard and Jan Mayen IslandsSwazilandSwedenSwitzerlandTaiwan, Republic of ChinaTajikistanTanzania, United Republic ofThailandTimor-LesteTogoTokelauTongaTrinidad and TobagoTunisiaTurkeyTurks and Caicos IslandsTuvaluUgandaUkraineUnited Arab EmiratesUnited KingdomUnited States of AmericaUruguayUS Minor Outlying IslandsUzbekistanVanuatuVenezuela (Bolivarian Republic)Viet NamVirgin Islands, USWallis and Futuna IslandsWestern SaharaZambiaZimbabwe
I have read and agree with the Privacy policy and the Cookie policy .
I agree to receive email updates from ABBYY Solutions Ltd. such as news related to ABBYY Solutions Ltd. products and technologies, invitations to events and webinars, and information about whitepapers and content related to ABBYY Solutions Ltd. products and services.
I am aware that my consent could be revoked at any time by clicking the unsubscribe link inside any email received from ABBYY Solutions Ltd. or via ABBYY Data Subject Access Rights Form .
Referrer
Last name
Query string
Product Interest Temp
UTM Campaign Name
UTM Medium
UTM Source
ITM Source
GA Client ID
UTM Content
GDPR Consent Note
Captcha Score
Page URL
Connect with us
Also read:
- [New] Effective Color Difference Filters in Film-Making
- [Updated] Perfect Pan & Tilt for Clearer Captures
- [Updated] Recording Tech Evaluation Blueprint
- [Updated] Strengthening Bonds Networking Tips for YouTube Content Creators
- [Updated] Superior MP4 Channel Updater for 2024
- [Updated] The Ultimate Zoom Setup Playbook
- [Updated] Unlocking the Full Potential of Zoom with YouTube Live
- 2024 Approved Subtle Harmonies on Desktop Systems
- 2024 Approved Tutorial for Downloading Movie Maker 6 on Windows
- How to Send Texts Without Using Up Your Mobile Plan
- In 2024, Prime Video Plus Comprehensive Live Channel Access
- In 2024, Ultimate Online Seminar Title Crafter
- In 2024, Ultra Creations Synopsis Studio 25 Detailed Analysis, 2023
- Transforming Perceptions with Virtual Tour Experiences for 2024
- Unlock iPhone 13 Without Passcode Easily | Dr.fone
- Unlocking the Power of Smart Lock A Beginners Guide for Xiaomi 13T Users
- Win AMD Radeon R9 Driver Update Guide
- Title: Mastering KYC Standards: An Exhaustive Manual on Procedures, Legal Frameworks, and Tech Integration
- Author: Christopher
- Created at : 2025-01-20 02:34:04
- Updated at : 2025-01-22 01:19:12
- Link: https://some-approaches.techidaily.com/mastering-kyc-standards-an-exhaustive-manual-on-procedures-legal-frameworks-and-tech-integration/
- License: This work is licensed under CC BY-NC-SA 4.0.